Cyber Security
Nowadays, every company is supplied by digital data flows with information, messages, financial transactions and with control and monitoring mechanisms. Along with the flow of energy and the flow of materials in manufacturing, your digital network is the third bloodstream in your business. And probably the most important – because your network controls everything. So it is at the top of your hierarchical structure!
And, to stay in the same metaphor, your network lives – it grows permanently – it changes permanently – it has „children“ – it moves across hardware and country borders and it communicates.
As with your own body, you should therefore always make sure that it is healthy, vital and armed against pathogens.
A complete failure of your network always results in immense damages:
- Temporary loss of production
- Disruption or failure of communication
- Loss of control in the supply
- Interruption of delivery
- Disruption or interruption of financial flows
- Loss of image and reputation
Thus, the permanent hardware and software related maintenance as well as the state-on-the-art expansion of your internal network is a mandatory prerequisite for the stability of your business, financial and administrative vitality but also for your competitiveness on the regional or global market.
But besides technical deficiencies, internal failures or individual errors, there is another threat to your business control – targeted attacks from outside by third parties.
Whether criminal motives (e.g. illegal enrichment through extortion), political influence by governmental, military or intelligence agencies of other countries or even market-related motives by competitors (industrial espionage, delay of technical innovation capability …) – your network is often the only and most vulnerable gateway for such illegal activities.
Often, new technologies to protect your data are evaluated as the sole tool and serve management as an argument of 100% invulnerability! Cloud-based data storage with its own encryption or VPN technologies are important, necessary and help enormously in securing your data. However, they are not the sole tool for digitally securing your business, nor do these tools provide 100 percent protection.
The battle between attacker and defender is an eternal up and down one, and experience from history shows that attackers usually have the advantage.
So anyone who claims to have established an absolutely secure system of protecting their own data and information has already lost.
If an attacker succeeds in gaining access to your network, then they have every opportunity to destroy, exploit and/or steal your internal business information.
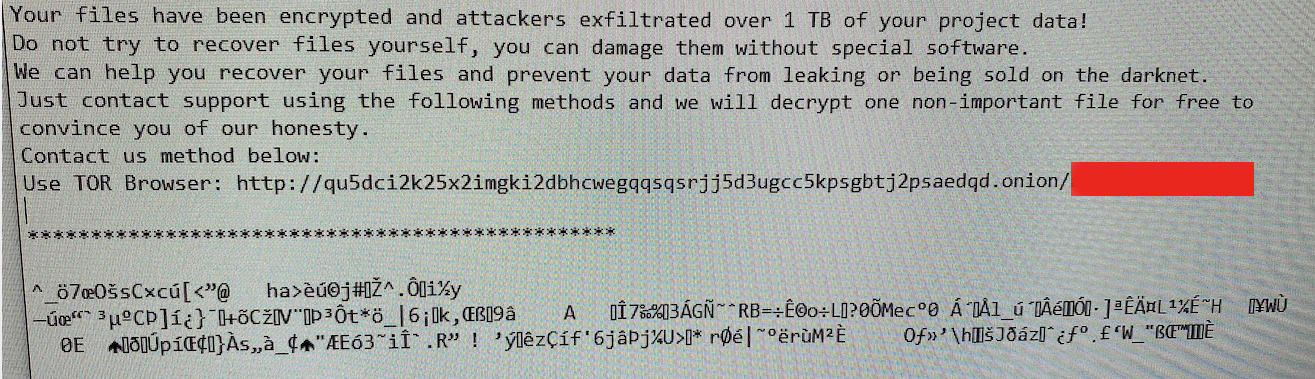
In recent years, and especially in recent months, small, highly specialized groups of cyber hackers have developed a methodology for illegally acquiring money – the so-called Ransom Attacks.
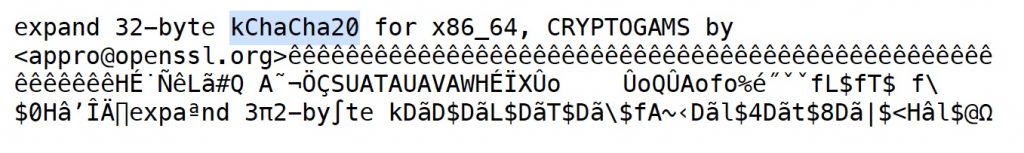
Here, the attackers use special methods to try to gain access to your internal network, and then run extremely efficient encryption programs over all or important parts of your network. Since these are often based on the most modern encryption technologies (ChaCha20, AES256 …), your encrypted data is de facto lost for you WITHOUT the help of the attackers. Moreover, the attackers can also download significant or even explosive information from your data pool with the intention to sell it on the darknet or otherwise to interested parties.
What is important to prevent such crisis situations?
What to do in the worst case?
How can you master the crisis with the least damage?
In addition to the already above-mentioned security of your network on the highest level, you need an absolutely access-proof backup. Modern tape library backup systems are particularly suitable for this purpose, as they generate a current status of the data and the organization of the network at short intervals and cannot be touched by external attacks. Thus, even in a worst-case scenario, a fast recovery of your source data is feasible. Even in such a case, there is „only“ the danger of information leakage.
But even here well-structured relational databases can help in advance, of course encrypted, at least partially!
However, if attackers have successfully encrypted your system and your backup server(s) are infected too you stack in the worst case scenario! Even the help of data rescuing companies will not change your situation essentielly! Without a decryptor tool from the attackers you will be not able to recover your data, your complete system!
Now the perpetrators vehemently pushing for the payment of ransom demands, we STRONGLY recommend that you call in experienced and successful negotiators.
With the right negotiation strategy, even in such a critical situation, significant potential savings can still be activated. This can both ensure the survival of your company but also significantly assist in the investigation of the crime (and thus the apprehension of the perpetrators -well, the chance is more than small!). Depending on the motive, this can also be extremely helpful in supporting a possible recovery action.
As with many other cases, the good old saying „Never say never!“ applies here, both in organizing the protection of your network and in dealing with a worst-case scenario and its aftermath.
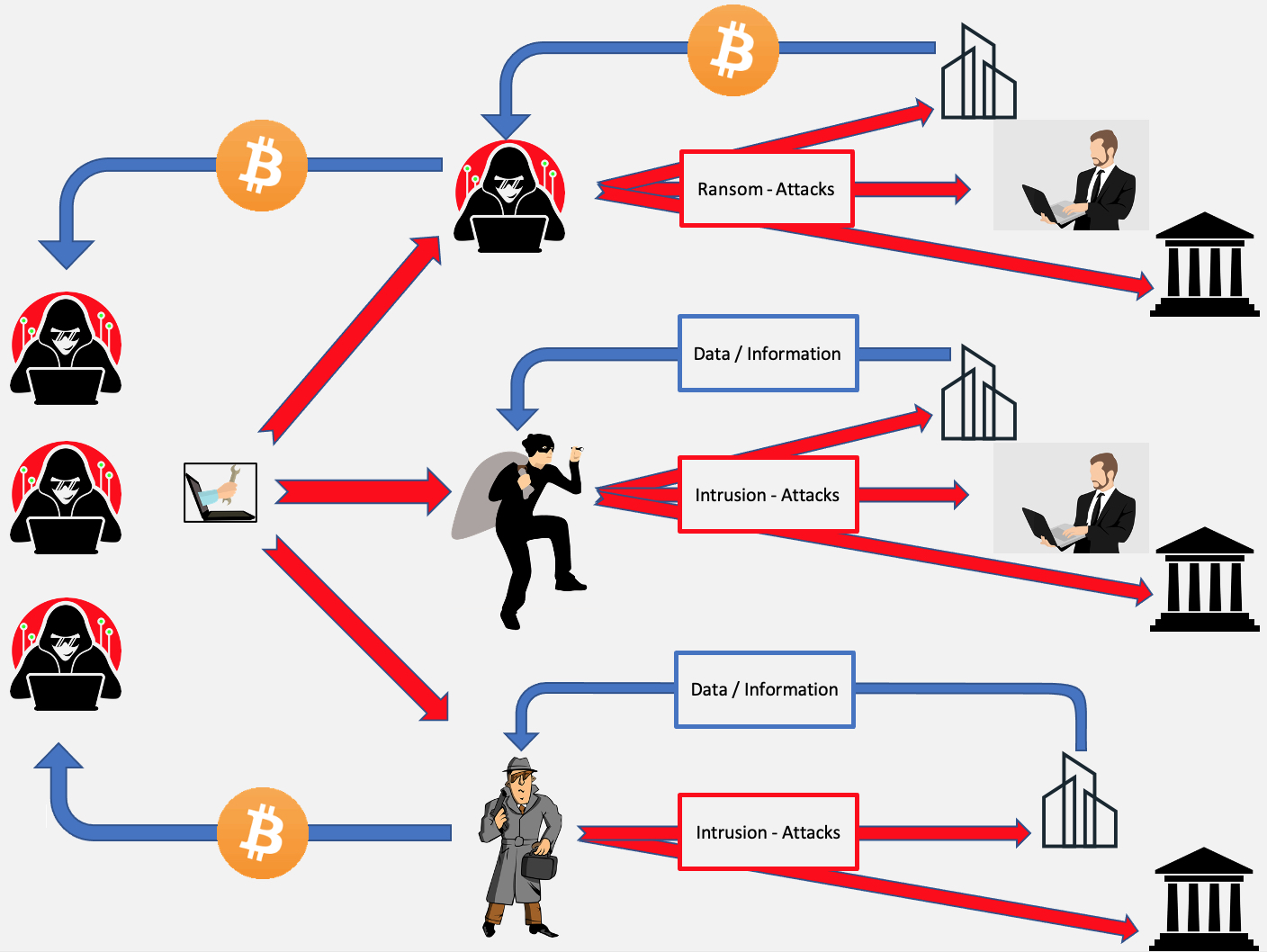
Ransomware-as-a-Service model (RaaS)
Various groups of criminal software developers have programmed special encryption tools in recent years. Even at the beginning of this phase, some of these groups used their tools themselves (GrandCrab [Golden Garden], DarkSide, BlackSuit…) to carry out ransom attacks against private individuals, companies and organizations. Often, these individuals also teamed up with relevant hackers to organize more efficient and targeted attacks.
Special groups (e.g. REvil) configured their software so that Russian or companies from countries of the former Soviet Union were not attacked (special exclusion of IP addresses on these territories or voice recognition).
Another stage in the evolution of Ransom Attacks is the RaaS model listed on the left.
Here, the designated groups sell their tools to other criminals (including economic spies and the like). Sometimes the „sellers“ act as service providers and profit proportionally from the illegal profits of the real initiators.
The specialised experts of ARROWS Consulting is among the most experienced and best negotiators of ransomware attacks. With the support of our forensic capabilities at the highest level, our expertise in cyber analytics and our skills in tracking such cyber-attacks, we offer you exactly the help you need in these situations – and this fast, successfully and confirmed by many customers.
We support you in the event of cyber attacks on three different levels, which, however, belong closely together:
1. management of the worst case scenario
2. follow-up investigations
3. support in reorganization of your internal and external data structure (network)
- ARROWS services include:
- Worst-Case Scenario:
- Detail determination of the actual situation
- Verification with regard to damage reduction through the use of external tools (data recovery, already existing decryptors)
- Parallel forensic investigation (attempt to assign the acting offenders to an already known group of offenders)
- If necessary running/leading (criminal-psychologically underpinned and in accordance with the management and with or without the responsible state authorities) the substantive and financial negotiations with the attackers
- If necessary: Preparation of the digital transfer of the ransom
- Ensuring that the necessary decryption tools (decryptors) are provided and that their functionality is faultless
- Conducting the post-negotiations
- After and during the entire time of the ransomware attack: monitoring of the darknet for possible illegal releases of internal data (leaking and/or sales activities)
- Emergency response / legal communication (PR)
- Follow-Up Investigation:
- Additional further investigations basing on data out of the restored network structure for better determination of the offenders (if not already done)
- Verification/monitoring of money flow (confirming receipt of payment on the perpetrator wallet and subsequent movement of money from this wallet to others [cryptocurrencies: Bitcoin, Dash, Monero and others]).
- Advisement based on the evaluation of the data and facts determined by own and/or other measures
- Re-investigation to rule out the possibility of internal complicity (very important for the security of the new, restructured data network)
- Scrutiny and Re-Organization:
- Intrusion test of the existing IT structure
- Consulting on structural changes to the new or existing organization-internal data network to significantly increase security
- Establishing a dedicated corporate/organizational task force based on a detailed response program in the event of a cyberattack